Good Hacking Examples
What is hacking? the top 5 examples you need to know.
Real-world examples. here are some of the most notorious examples of malware infection, demonstrating the methods and techniques hackers use to penetrate systems. these security breaches have cost computer users inestimable amounts of time, frustration, and money. koobface. an anagram of facebook, koobface was a hybrid, or blended threat, malware. Social media features in a lot of our growth hacking examples, and with good reason. it’s an extremely cost-effective way to promote anything. knudge. me, an app to help people level up their english-speaking skills, used social media and in-product marketing to drive growth from 100,000 to 1 million users within six months.

100 Incredible Life Hacks That Make Life So Much Easier
Consider an example where an employee gets good hacking examples fired from a company. he might hack the company's website and deface it with lewd photos and words as vengeance for losing his job. this type of hack is obviously wrong because the company didn't ask for it. Jan 23, 2017 · i always liked to use the ransomware virus as a good example of hacking as i think that it’s something really smart, sick of course, but smart nonetheless.
Although hacking can be used for good, most attacks are carried out for the benefit of the hackers responsible for them. read on to learn about the main types of hacking and the most commonly used hacking techniques. what you will find out in this article: what is hacking; what types of hacking exist? examples of hacking techniques. White hat hacking; commonly referred to as ethical hacking, white hat hacking is always used for good. instead of being the stereotypical renegade whiz kids you see in movies, white hat hackers are often employed or contracted by major companies to help them improve their security by identifying vulnerabilities in their system. A good password should balance the ease of remembering it with the complexity to resist being guessed by hacking programs. here are some tips. a good password should balance the ease of remembering it with the complexity to resist being guessed by hacking programs. examples of weak and strong passwords these are the best passwords to secure.
May good hacking examples 24, 2017 · it's the white hat hackers that really do good work, however, by hacking into sites in order to help those sites test and improve their security so that the other types of hackers can’t gain access so easily. all three groups use the same methods, but their motives are very different. For example, a dictionary hacking tool would attempt these iterations of the word dog: dog password-guessing tools submit hundreds or thousands of words per minute.
What Are Some Great Examples Of Ethical Hacking Quora
Sep 23, 2019 · good hackers are also called white hats or security hackers, and bad hackers called crackers or black hats. a good and bad hacker work in much the same way and even use identical skills to perform the hacking, so what makes one better than the other?. 23 proven growth hacking examples you can steal to gain traction 1. airbnb. let’s kick things off with one of the most famous growth hack examples: the airbnb craigslist hack. 2. dollar shave. we’re always saying that video marketing is a great marketing technique, and another of our famous 3. Using simple hacks, a hacker can be able to know about your personal unauthorized information. knowing about these common hacking techniques like phishing, ddos, clickjacking, etc. could come. More good hacking examples images.
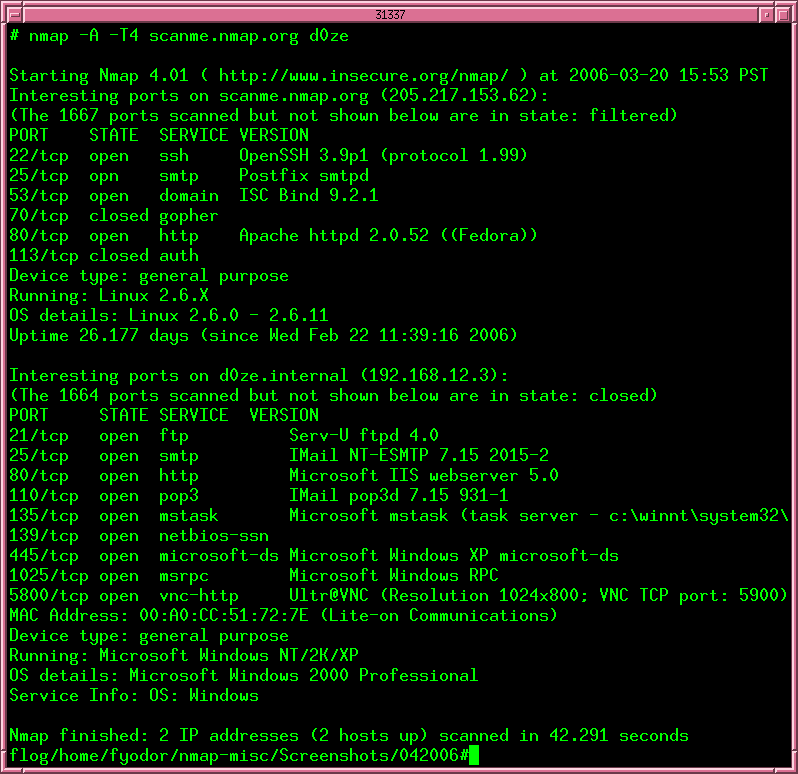
One example is to map a entire network not only 1st bridge that ur on. this may also mean to use arp pings (arp poisoning a network). arp ping may also be used as ddos but in our case is for maping. of course nmap already does this but understanding how it works is a different thing. Jul 17, 2018 · ethical hacking is using hacking for a good cause. instead of hacking into a computer system to steal information or cause issues for a company, the hackers learn about security vulnerabilities in order to help the company fix any issues that might be present to improve the security of their network. Be sure to check out our ultimate guide to growth hacking for more strategies, examples, and tools you can use to skyrocket your business. that’s it! with these 13 growth hacking strategies, your good hacking examples business is poised for growth. next, check out more growth hacking examples for more inspiration.
The 15 biggest data breaches of the 21st century data breaches affecting millions of users are far too common. here are some of the biggest, baddest breaches in recent memory. Explore 85 hacking quotes by authors including henry david thoreau, henry rollins, and kevin mitnick at brainyquote. "my actions constituted pure hacking that resulted in relatively trivial expenses for the companies involved, despite the government's false claims. ". I always liked to use the ransomware virus as a good example of hacking as i think that it’s something really smart, sick of course, but smart nonetheless. basically, this virus encrypts all of your files and asks for a ransom in exchange for the.
Examples of bad passwords hackers and computer intruders use automated software to submit hundreds of guesses per minute to user accounts and attempt to gain good hacking examples access. these tools use lists of dictionary words to guess the password sequentially. The 5 worst examples of iot hacking and vulnerabilities in recorded history. iot hacking can be extremely effective, producing ddos attacks that can cripple our infrastructure, systems, and way of life.
I always liked to use the ransomware virus as a good example of hacking as i think that it’s something really smart, sick of course, but smart nonetheless. basically, this virus encrypts all of your files and asks for a ransom in exchange for the decryption keys. Three good ones to look into are kava-kava, st. john’s wort, and rhodiola rosea. Knowing about these common hacking techniques like phishing, ddos, clickjacking, etc. could come handy for your personal safety.
Good hacking is to protect and learn, while bad hacking is for destruction. hacking has a good and a bad side, depending on the intention. good hacking is to protect and learn, while bad hacking is for destruction. examples of famous hackers. johndwilliams / istock editorial / getty images plus black hat. Real-world examples koobface. an anagram of facebook, koobface was a hybrid, or blended threat, malware. it used the trickery aspect of a mac flashback. mac flashback attacks almost always occurred without the victim’s knowledge, as apple mac users found out zeroaccess. the zeroaccess rootkit. Bug bounty programs rewarding responsible disclosure of security flaws. how does one become a bug bounty hunter?.
Komentar
Posting Komentar