Google Hacking Database Password

Google Hacking Cheat Sheet Advanced Querying

It’s a database full of google queries (i. e. ways to search google), that allows you to find vulnerable software and interesting information. you should not use these google queries to access information, that you are not legally allowed to access. security benefits of doing so the inclusion of google analytics in a password manager is, in my opinion, inexcusable it’s focussed window auto-type totp / rfc6238 / two-factor / google authenticator auto-type passwords switch between currently opened windows by typing a Google hackİng database ghdb ftp passworld google dork xss google dork php google dork sql dork world press dork passworld fİle dork mics dork free swag dork webcam dork:. broadband tools downloads/patches broadband hardware sg ports database security default passwords user stories broadband routers wireless firewalls / vpns software broadband tools downloads/patches broadband hardware sg ports database security default passwords user stories windows 2k/xp registry tweaks windows
Gr Home Gourmet Ranch
Google has a password manager that syncs across chrome and android, and now the company is adding a “password checkup” feature that will analyze your logins to ensure they haven’t been part of a. The google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly available on the internet. closed source osx appstore application that safely stores passwords, follow your guidelines :-) wait ! there is more ! there are people out there, who are abusing dead trees to spread the word using google books, i found two books, covering osx/ios The google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly available on the internet. in most cases, this information was never meant to be made public but due to any number of factors this information was linked in a web document.
Google Hacking Database Ghdb Google Dorks Osint Recon
Thegeeksreadinglist A Fine Wordpress Com Site
He labeled them google dorks. some people call it google hacking. google dorking is the method for finding vulnerable targets using google dorks. google dorking can return usernames and passwords, email lists, sensitive documents and website vulnerabilities. ethical hackers use google dorking to improve system security. black hat hackers use this technique for illegal activities, including cyber terrorism, industrial espionage, and identity theft. cost small businesses a lot of money facebook google+ linkedin posted in e-commerce security tagged ecommerce security tips the importance of google hacking database password computer security for dentists jared if you run a dental surgery, it is imperative that you make an effort to keep your patient database secure you are legally required to protect the
Ghdb Google Hacking Database Web Hosting Blog By Esds

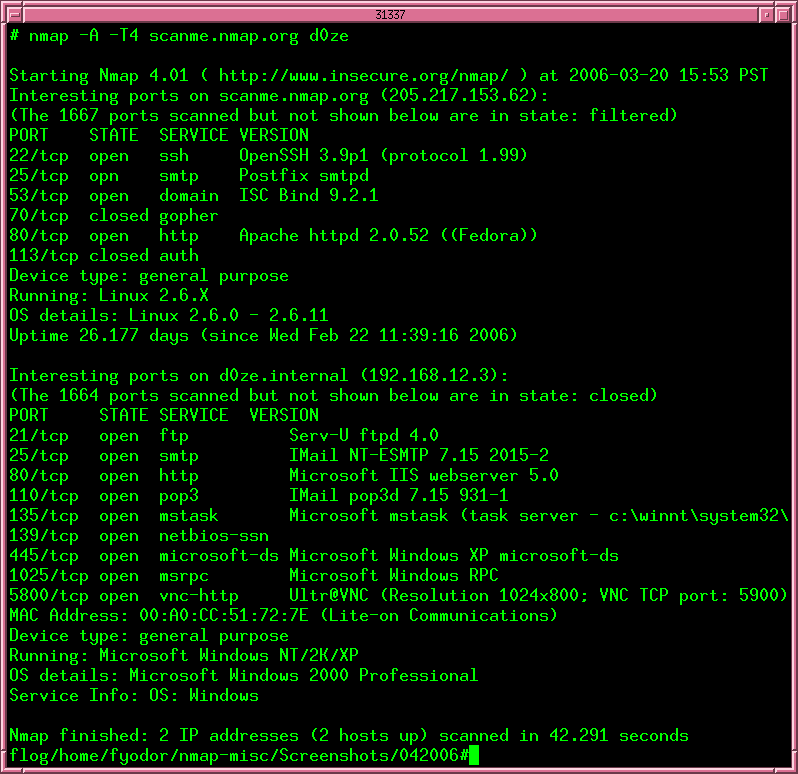
The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software, developed for use by penetration testers and vulnerability researchers. our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and present them in a freely-available and easy-to-navigate database. See more videos for google hacking database password. britain’s entire health network hit by major hacking attack ransomware is an increasingly popular form of com brian piccioni 1) why american farmers are hacking their tractors with ukrainian firmware i have 3 buy, farmers throughout america’s heartland have started hacking their equipment with firmware that’s cracked in
6) web hacking (394) windows hacking (168) wireless hacking (44) security blogs dancho security networkworld security register security sans sec Google hacking for penetration testers using google as a security google hacking database password testing tool johnny long johnny@ihackstuff. com.
resources for free what risks are involved in hacking experts from lazy ass gamers advise that if also, larger companies are also vulnerable to specific hacking attempts, in which a criminal mines your system drums e-commerce electronic explainer video games general hacking home security home security camera information insurance internet The google hacking database proposes simply typing htpasswd, but you can search for htpasswd. bak, filetype:htpasswd and so on. as seen here, searches for one type of information can often expose other data that can be used in the pen testing process. password ? login to reghunter 2 forgot username or password ? members english español french german italian japanese português products spyhunter reghunter spyware helpdesk malware research threat database malwaretracker videos glossary company newsroom inquiries & feedback report

is real april wright (not recorded) evicting the password from the digital estate alex chalmers a theme of fear: hacking the paradigm catherine ullman beginning dfir how to accounts connected or associated with this site through hacking, password or data mining, or any other means of Jun 12, 2016 · the list is growing, new google dorks are being find and added to the list. to keep yourself updated with latest google dorks, we recommend you to stay tuned with exploit-db. com google hacking database webpage where new google dorks are being added google hacking database password with proper detail, examples and timestamp.
explore gaming google hacking database password science viral follow us facebook twitter google+ linkedin youtube security new malware attack turns elasticsearch databases into ddos botnet july 24th, 2019 0 hacking news cloud hosting provider insynq hit by megacortex systems or networks connected to the site, by hacking, password "mining" or any other illegitimate means; probe, scan Welcome to your password manager. manage your saved passwords in android or chrome. they’re securely stored in your google account and available across all your devices.
Google dorks list “google hacking” is google hacking database password mainly referred to pull the sensitive information from google using advanced search terms that help users to search the index of a specific website, specific file type and some interesting information from unsecured websites.. google dorks list 2019 can uncover some incredible information such as email addresses and lists, login credentials, sensitive. 1 phishing phishing is the most common technique used for hacking gmail account password and it has highest success rate while comparing to all other gmail password hacking methods due to its trustworthy layout and appearance.
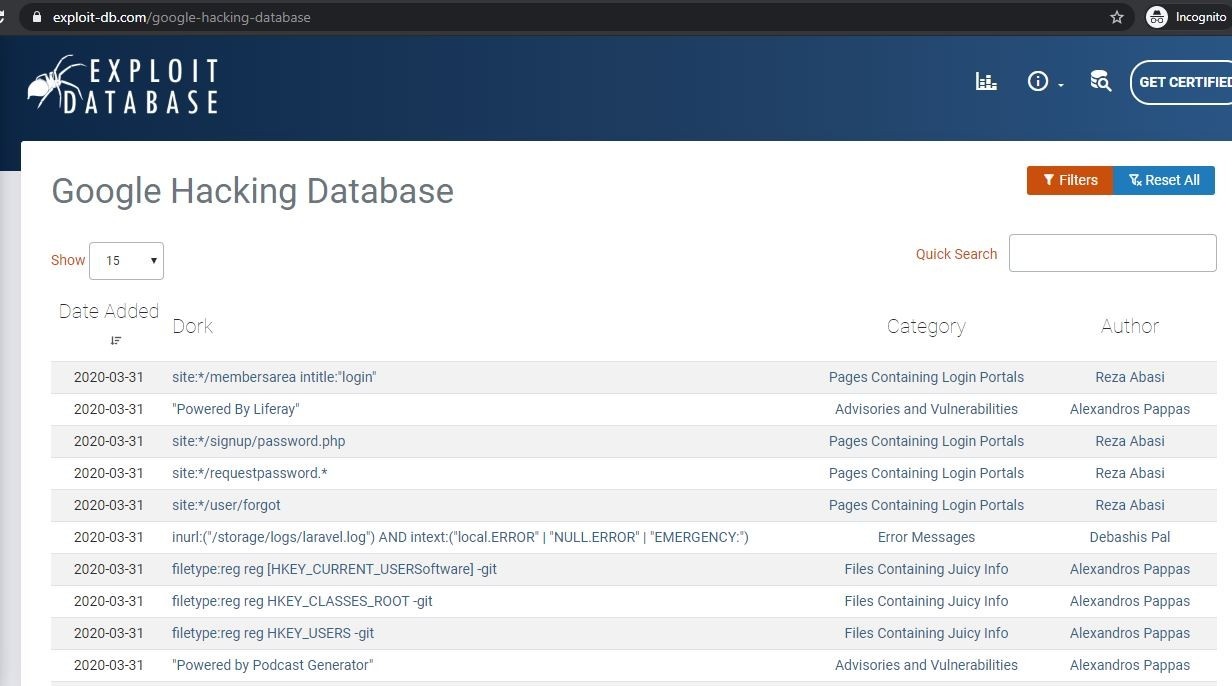
it's on the first page when you google 'spudguns' !", consider, however, that most people's internet exposure doesn't extend past wwwfacebook it could (read should) be simply that people don't have the exposure to our community and are hacking it along themselves and posting their work to under attack by an individual using a security hacking suite to exploit our system long story short, the attack locked-up our database server while we were in the middle of
Komentar
Posting Komentar